Abstract
- SDLC Polling
- How SDLC differs from HDLC / X.25 Level 2
- SDLC - what frames you would expect to see on the link
- SDLC frame types and protocol
- Relationship to SNA and QLLC
- recognize common SDLC problems on PSS
1.0 - Introduction
SDLC is a protocol developed by IBM, unlike Bi-Sync it separates the link
control functions from the character set and data content. HDLC was later defined
as an international ISO standard and this was used as the basis of X.25 link
layer.
SDLC ferforms the following functions:
- Transmits message unit across links
- Manages link-level flow
- Manages error recovery procedures for transmission errors, Adjacent nodes in a SNA network are connected by one or more links.
The following types of physical link are supported by SDLC
- Data Channels a data channel transmits bits in parallel, because of this channel-attached nodes must be located fairly close to one another
- SDLC links this is the most common method of connecting remote nodes together.
- X25 interface remote nodes can also be connected over a packet switched network using a protocol called QLLC (qualified logical link control) to carry the SDLC frames.
X21 interface remote nodes can also be connected over a circuit switched network
1.1 - SNA
- SNAs datalink layer uses SDLC.
THE DATA-LINK LAYER
The data link layer provides functional and procedural means to establish,
maintain and release data-link-connections among network-entities and to transfer
data-link-service-data-units. A data-link-connection is built upon one or several
physical-connections.
FUNCTIONS OF THE DATA LINK LAYER
The data-link converts the unreliable datastream into a process to make sure
the bits that are sent are received correctly at the destination.
It beeaks up the stream of bits into blocks ("frames") of a reasonable size and adds some checking mechanism (usually a "cyclic redundancy check"). If the destination finds that the check is correct, it can assume that the data has been received without error; if the check is wrong, the destination assumes that there is an error in the data and requests the block to be retransmitted (either actively by sending an error indication or passively by not acknowledging the correct receipt of the block).
EARLY DATA-LINK PROTOCOLS
All the early protocols were " byte-orientated",
that is, they saw the data as a sequence of 8-b bytes. They used special characters
for control purposes (eg. to indicate the beginning and end of a block) and
thus were committed to a specific character code.
One of the problems of any protocols is "data transparency". That
is, the user wishes to send an arbitary data stream but the protocol itself
needs to use control characters which could occur within that data stream.
There are a number of solutions to this problem:-
1) Do not use some characters for data, eg. ASCII,
EBCDIC codes
2) Data Link Escape (DLE) (Character stuffing)
A special character DLE is used to indicate that th following character is
to be interpreted as a control character. Thus if ETX ("end of text")
is encountered in a block, not preceded by DLE, it is taken to be part of the
data. If the sequence DLE EJX is found, then it is taken to indicate the end
of text. If two DLEs are found, then it is assumed that only one DLE was in
the data.
3) Count Field Mechanism
Used in DDCMP (Digital Data Communication Message Protocol) PROBLEM - If the count field is corrupted then this could lead to serious inefficiencies so, for this reason, protocols using a count field nearly always have a checksum appended to the block header in addition to the ordinary checksum at the end
of the block.
BIT-ORIENTED PROTOCOLS
The data-stream is considered to be a sequence of bits with no arbitrary division
into bytes.
Bit-Stuffing - If the sender wishes to send a sequence of bits
containing (at least) five consecutive "1" bits, it inserts a "0"
bit after the five "1"s. Similarly, if the receiver detects five "1"
bits followed by a "0", it removes the zero. Such an algorithm can
very easily be implemented in hardware and is very efficient.
This transparency mechanism then allows sequences of more than five "1"s to be used for control purposes and bit-oriented protocols use the sequence "01111110" as a "flag" to delimit frames (and to synchronise sender and receiver).
2 - SDLC
A SDLC link can be configured as a point-to-point link or a multiple station
loop configuration consisting of a primary station and a number of secondary
stations.
All transmissions on a SDLC link are organized in the following form which
is known as a frame.
| Flag | address | control | Information | FCS | Flag |
2.1 - Address Field
This is a 1 byte field which identifies the secondary station(s), this can be:
- a specific link station address
- a group address
- a broadcast address FF=all stations
- a no stations address = 00
The primary station does not need an address since SDLC links use Normal Response Mode (NRM). A frame from the primary to the secondary is known as a 'command' and contains the address of the secondary, a frame from the secondary is known as a response and also contains the address of the secondary station. Hence responses can only be sent as a result of a command.
2.2 - Control Field
This is an 8-bit field for Modulus 8 working or a 16-bit field for Modulus
128 working, this field identifies the frame type as follows:
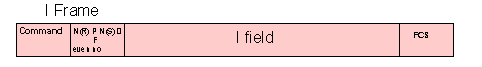
Frame Types
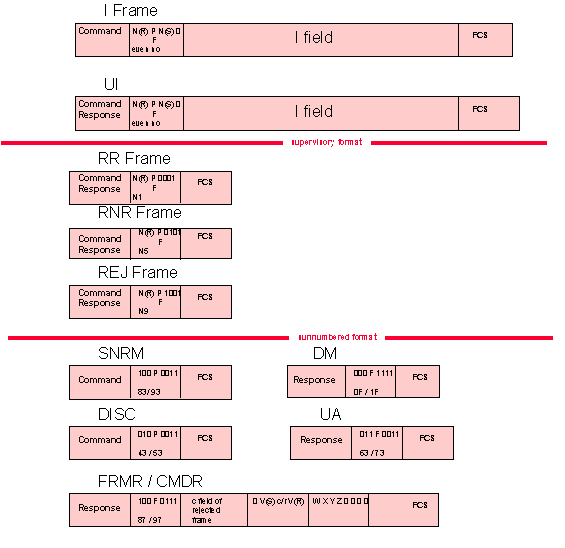
Types of SDLC frame
I Information
I frames are numbered. The Ns count provides for numbering the frame being sent and the Nr provides acknowledgement for the I frames received. When duplex ifformation exchange is in continual process, each station reports its current Ns and/or Nr counts in each I or S frame exchanged.
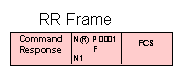
Supervisory frames
RR - Receive Ready
Sent by either a primary or secondary station, RR confirms numbered frames through Nr-1 and indicates that the originating station is ready to receive.
RNR - Receive Not Ready
Sent by either a primary or secondary station, RNR indicates a temporarily busy condition due to buffering or other internal constraints.
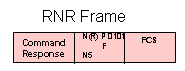
REJ - Reject
This command/response may be transmitted to request transmission or retransmission of numbered information frames. REJ confirms frames through Nr-1 and requests the retransmission of numbered information frames starting ae Nr contained in the REJ frame.
Unnumbered Format
UI - unnumbered Information
As a command or a response, a UI frame is the vehicle for transmitting unnumbered information.
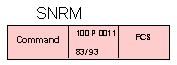
SNRM - set normal response mode
This command places the secondary station in normal response mode (NRM) for information transfer. UA is the expected response. The primary and secondary station Nr and Ns counts are reset to 0. No unsolicited transmissions are allowed from a secondary station that is in NRM. The secondary station remains in NRM until it receives a DISC or SIM command.
DISC - Disconnect
This command terminates other modes and places the receiving (secondary) staton in disconnected mode. The expected response is UA. A secondary station in disconnected mode cannot receive or transmit information or supervisory frames.
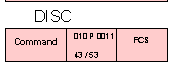
RD - Request Disconnect
This request is sent by a secondary station desiring to be disconnected (by the DISC command)
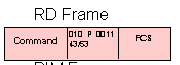
UA - Unnumbered Acknowledgment
This is the affirmative response to an SNRM, DISC or SIM command
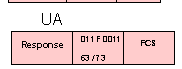
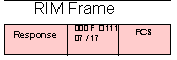
RIM - Request Initialisation Mode
A RIM frame is transmitted by a secondary station to notify the primary station of the need for a SIM command
SIM - Set Initialisation Mode
This command initiates system-specified procedures for the purpose of initialising link-level functions. UA is the expected response. The primary and secondary Nr and Ns counts are reset to 0.
DM - Disconnected Mode
This response is transmitted by the secondary station to indicate that it is in the disconnected mode.
FRMR - Frame Reject
This response is transmitted by a secondary station in NRM only when it receives an invalid frame. A received frame may be invalid for several reasons:
- its C field is not implemented at the receiving station. This category includes unassigned commands.
- the information field is too long to fit the receiving station buffers
- The C field in the received frame does not allow an I field to be received with the frame.
- The Nr that was received from the primary station is invalid.
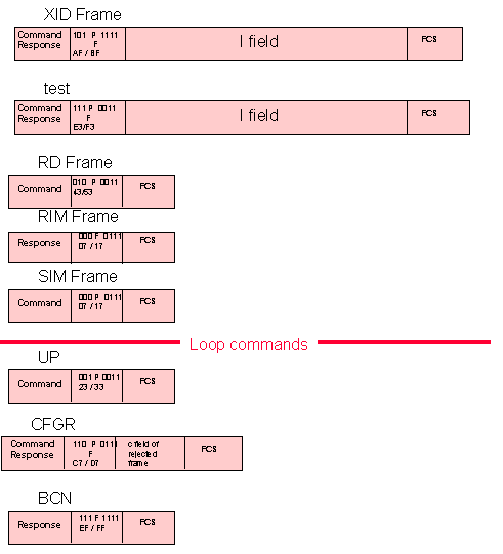
TEST - test
As a command, a test frame may be sent to a secondary station in any mode to solicit a TEST response. If an information field is included with the command it is returned in the response.
XID - Exchange station Identification
As a command, XID solicits the identification of the receiving (secondary) station. An information field may be included in the frame to convey identification of the transmitting (primary) station. An XID response is required from the secondary station. An information field in the response may be used for identification of the responding secondary station.
Loop Commands and responses
UP - Unnumbered Poll
with P bit = 0:
An optional response poll is sent out by the primary station to poll one station, a group of stations, or all the stations on the loop. A response is not necessarily required.
with P-bit = 1:
A mandatory response poll is addressed to an individual station, group of stations, or all of the stations on a loop. It serves to perform an unnumbered poll of the addressed secondary stations. A polled station will respond either with frames it has waiting to transmit or retransmit, or, if no such frames exist, with another appropriate response (RR,RNR or DM).
CFGR - Configure
Command:
The configure command contains a function descriptor (a subcommand) in a single-byte information field.
Subcommands:
| 00000000 | Clear |
| 0000001x | Beacon test |
| 0000010x | Monitor Mode |
| 0000100x | Wrap |
| 0000101x | Self-test |
| 0000110x | Modified Link test |
RESPONSE:
The configure response is transmitted by secondary stations only in response
to a configure command. The structure of the configure responses are identical
to those of the configure commands. If the low order bit in the information
field of the response is set to 1, the configure function in the information
field has been set. If the low-order bit in the information field is set to
0, the configure function in the information field has been cleared.
BCN - Beacon - response
When the secondary station detects the loss of communication at its input, it begins to transmit a beacon response. This allows the primary station to locate the problem in the loop and to take appropriate action. In the beacon response, the F-bit can be either a 1 or a 0. As soon as the input resumes normal status the secodary stops transmitting the beacon response.
Link States
Bringing a link up
Primary __________________Secondary
------- SNRM P (command) ------>
------- SNRM P (command) ------>
------- SNRM P (command) ------>
<------ UA F (response) --------
Primary station polls with SNRM's with the P-BIT set to 1, when the secondary
station is ready it responds with a UA with the P-BIT set to 1.
Information Transfer
primary to secondary -
------- I P (command) --------->
<------ RR F (response) -------
Primary can send an I frame at any time the link is up, the secondary can
acknowledge this with either of RR,RNR,REJ or I frames.
secondary to primary -
| ------- RR P (command) --------> | Poll |
| <------ RR F (response) -------- | Nothing to send |
| ------- RR P (command) --------> | Poll |
| <------ I (response) -------- | 1 to 7 I frames depending on |
| <------ I (response) -------- | window size can be sent in response |
| <------ I F (response) -------- | to poll final I frame has F bit to indicate turn round of line |
Taking Line Down
Initiated by primary station -
Primary__________________ Secondary
------ DISC P (command) ------->
<----- UA F (response) --------
Initiated by secondary station -
------ RR P (command) --------->
<----- RD F (response) -------- | Request disconnect
------ DISC P (command) ------->
<----- UA F (response) --------
STANDARDS
ISO 3309 "HDLC Frame structure"
ISO 4335 "HDLC Elements of protocol"
ISO 6159 "HDLC - Elements of procedure - unbalanced classes"
ISO 6256 "HDLC - Elements of procedure - balanced classes"
CLITT X25 Level 2 (1984 revision) is known as LAP-B and this is
a balanced HDLC procedure with all the options determined.
1 - The link layer
* Link layer - could also be called, frame level
link level
frame layer
level 2
The link layer provides the following services:
- byte synchronisation
- Divideing the datasteam into packets
- Error detection and recovery
- Link level flow control
- Link establishment and release.
.............................................
. .
. .
. ......... ......... . ------------
. .... PSE d ......... PSE f ..........-| |
----------- . . ......... ......... . | computer B |
| | ......... . . . |------------|
| computer A|--. PSE c . . . .
|-----------| ......... . . .
. . ......... .
. ............. PSE e . .
. ......... .
. .
.............................................
* At the link level each 'hop' through the network is independent.
that is -
If computer A has a packet to send to computer B
computer A 'wraps' packet into frame and sends it to PSE c
PSE c 'unwraps' the packet and decides where to send it - say PSE d
PSE c 'wraps' the packet in a completely new frame and sends it to PSE d
this continues until the packet reaches computer B
so the link header and trailer bytes
will be different for each 'hop'
* Strictly standards such as X.25 only define the protocol between the network and customers computer, however in practice, the link level between two Packet Switching Exchanges will be similar or identical to X.25 level 2.
- The link layer contains no routing info that is all handled by the packet layer - all the link layer does is safely transfer the packet across the hop.
- Any protocol events at the link level - eg disconnect or flow control affect all calls on the link.
Slide LNK1 - Purpose of Link Layer
2 - Synchronisation
Bit Sychronisation
Bit synchronisation is derived by the modem from the incoming datastream.
There is a option in SDLC called Non Return to Zero Inverted (NRZI), this is designed to ensure that there are plenty of bit transitions in the data to help with bit synchronisation, this is not required by modern modems.
byte Synchronisation
Byte synchronisation is how the receiver knows where, in the serial datastream,
one character stops and the next one starts.
In Asynchronous this is done by stop and start bits, this is simple but inefficient.
In Bisync it is done by the SYN character, this means that the SYN character
cannot be used in normal data without using a special protocol.
In SDLC/HDLC/X.25 it is done by sending a flag:
Any sequence of six ones with a zero on either side is a flag -
eg flag = 01111110 = 'hex 7E'
* The flag has a dual purpose, it provides byte synchronisation and provides
a marker of the beginning and end of a frame, so between frames there must be
one or more flags.
* When there are no frames to send then flags are normally sent continuously
the only exception is IBM SDLC which sometimes stops sending flags between frames.
* The sequence 01111110 could occur by chance in the data being sent which would cause a false flag to be detected. To stop this happening an extra zero is inserted after any sequence of five ones and this extra zero is removed at the distant end. This is known as 'bit stuffing'.
Slide LNK2 dividing the datastream into frames
Example 2 - flags and bit insert/delete
Analysing directly from the bits on the line is not something you will need
to do in practice because all protocol testers do this automatically.
However try this example to get an insight into how the datastream is divided
into frames.
Here is another example worked through
0100110111111011000000111110100110110100011011101111110110
----><------> ^ <------><---
end of this a zero flag start
last pattern following of next
frame must be five ones frame
a flag must have
wherever been inserted
it occurs for transparency
so remove it
this leaves the following,
1100000011111 1001101101000110111
divide up into bytes,
11000000 11111100 11011010 00110111
<---------------->
the sixteen bits
before the flag is
always the frame
check sequence
<------>
this is the
control byte
the LSB is
transmited
first so it
is 3F in hex
which identifies
this as a SABM
frame.
<------>
this is
03 in hex
which is
address A
Now try the example yourself - dont worry about what type of frame it is - just decode it to HEX
4 - Link States
Idle channel state - more than 15 ones
The action to be taken by a DCE upon detection of the idle channel state is
not defined at this time.
active channel state - sending a frame or continuous flags
Disconnected phase - Set on DISC-UA exchange or expiry of timer T3. currently
PSS polls with DISC frames in this state.
Information phase - Set by SARM-UA, SABM-UA, SABME-UA etc.
* when no data - time fill - continuous flags
- known as - active channel state
- useful test - flags shows RX line OK
Slide LNK14 - Link states
5 - Frame structure
All transmissions on a X.25/HDLC/SDLC link are organized in the following
form which is known as a frame.
---------------------------------------------------
Flag | address | control | Information | FCS | Flag
|---------------------------------------------------|
8 bits 8 bits n bits 16 bits
see note 1 seeote 2
Note 1: Some recommendations define modulo 128 operation but PSS does not
support these. When modulo 128 is used 16 bit control field is used for frame
formats that contain sequence numbers.
Note 2: The information field is only used in some frame types. In the case
of I-frames the length of the field is not restricted by the link layer, although
restrictions may be imposed by higher layers in the protocol, eg maximum length
or integral number of bytes.
Note 3: Addresses and control fields shall be transmitted with the low-order bit first (for example the first bit of the sequence number that is transmitted shall have the weight 2^0).
Slide LNK3 - Frame Structure
6 - Address Field
SDLC
Like other IBM protocols such as bi-sync, SDLC works in a polling environment
this allows a point-to-point link or a multiple station loop configuration consisting
of a primary station and a number of secondary stations.
The address field is a 1 byte field which identifies the secondary station(s), this can be:
- a specific link station address
- a group address
- a broadcast address FF=all stations
- a no stations address = 00
The primary station does not need an address since SDLC links use Normal Response
Mode (NRM). A frame from the primary to the secondary is known as a 'command'
and contains the address of the secondary, a frame from the secondary is known
as a response and also contains the address of the secondary station. Hence
responses can only be sent as a result of a command.
8 - Information Field
In the case of I-frames the information field contains the packet level information,
this is the point of the whole link layer - to get this information across the
link safely, the contents of this field are covered in the packet layer.
In the case of FRMR frames the information field contains 3 byte
s which contain information about the reason for the reject.
There is no theoretical maximum length of the I-field, the practical maximum
length will depend on the error rate, if the error rate is high and the frames
are long the retransmission overhead will become unacceptably high.
Parameter N1 defines the maximum length of the I-field, also the packet level allows a maximum length for packets to be negotiated. Some networks including PSS require that the I-field contain an integral number of bytes although there is nothing in the protocol that requires this.
slide LNK12 - error detection
slide LNK13 - error correction
FCS field - Error detection and recovery
During transmission bits can be corrupted due to causes such as Gaussian noise,
thunderstorms at Reading exchange etc. These bit corruptions tend to happen
in bursts, for example, a 10ms noise burst induced from electomechanical devices
in a telephone exchange could zap 96 bits at 9600 baud.
The link layer needs to provide error free transmission in both directions,
despite the possibility that any transmission could be hit. This also has to
be done without slowing down the throughput.
The way this is done is to keep a copy of each frame at the sending end, while
it is transmitted to the distant end with an error check, only when the receiving
end sends back an acknowledgement that the frame has been received without error
can the transmitting end delete its copy. This is much more efficient than duplicating
or triplicating the data to correct errors.
Error detection
There are a number of possible methods of error detection:
* Parity bit on each character - This has the following disadvantages,
a) Uses 1 bit in every byte so only 7 bits are left for data, this means that it can only be used for ASCII characters without transparent 8-bit data.
b) An even number of errors will not be detected.
c) High overhead, ie 1 in 8 bits do not carry useful data.
d) There in no standard about whether even or odd parity is used.
* Longtitudinal parity byte
- last byte in a block of data contains a parity byte, this still has the disadvantage
that an even number of errors in any row would not be detected.
* Hamming codes - The principle of parity checks can be extended by adding more bits this can also allow errors to be corrected without being re-transmitted. This has the disadvantage of using more bits and therfore being even less efficient.
* Polynomial code - also known as a cyclic redundancy code (CRC) or frame
check sequence (FCS). This uses a different form of arithmetic, the rules are
the same as binary arithmetic except that there are no carries.
polynomial addition and subtraction thus become the same as 'exclusive or'
on each corresponding pair of bits.
polynomial division is therefore done as follows:
1 1 0 0 0 0 1 0 1 0 <--- result
----------------------------
1 0 0 1 1 ) 1 1 0 1 0 1 1 0 1 1 0 0 0 0
1 0 0 1 1 | . . . . . . . .
--------- v
1 0 0 1 1 . . . . . . . .
1 0 0 1 1 | . . . . . . .
--------- v
0 0 0 0 1 . . . . . . .
0 0 0 0 0 | . . . . . .
--------- v
0 0 0 1 0 . . . . . .
0 0 0 0 0 | . . . . .
--------- v
0 0 1 0 1 . . . . .
0 0 0 0 0 | . . . .
--------- v
0 1 0 1 1 . . . .
0 0 0 0 0 | . . .
--------- v
1 0 1 1 0 . . .
1 0 0 1 1 | . .
--------- v
0 1 0 1 0 . .
0 0 0 0 0 | .
--------- v
1 0 1 0 0 .
1 0 0 1 1 |
--------- v
0 1 1 1 0
0 0 0 0 0
---------
0 1 1 1 0 <---- remainder
in practice this can be computed by using a shift register as follows:
msb lsb
bit-16 bit-15 bit-0
----- ------------------------------------
|-----| |------------check register----------| <-- data shifted in
| --^-- --------|
|-------------| & |--<-| + |
O
|-----| |--------
------------------------------------
|----------- crc constant -----------|
This is normally built into the SDLC/HDLC chip.
X25 link level Frame check sequence (FCS) field
The notation used to describe the FCS is based on the property of cyclic codes that a code vector such as 1000000100001 can be represented by a
12 5
polynomial P(x)=x + x + 1. The elements of an n-element code word are thus
the coefficients of a polynomial of order n-1. In this application, these coefficients
can have the value 0 or 1 and the polynomial operations are performed modulo
2. The polynomial representing the content of a frame is generated using the
first bit received after the frame opening flag as the coefficient of the highest
order term.
The FCS field shall be a 16-bit sequence. It shall be the ones complement of the sum (modulo 2) of:
k 15 14 13 12 11 10 9 8 7 6 5
1) the remainder of x (x + x + x + x + x + x + x + x + x + x + x
4 3 2
+ x + x + x + x + 1)
16 12 5
divided (modulo 2) by the generator polynomial x + x + x + 1, where k is the number of bits in the frame existing between, but not including, the final bit of the opening flag and the first bit of the FCS, excluding bits inserted for transparency, and
2) the remainder of the division (modulo 2) by the generator polynomial
16 12 5 16
x + x + x + 1 of the product of x by the content of the frame,
existing between but not including, the final bit of the opening flag and
the first bit of the FCS, excluding bits inserted for transparency.
As a typical implementation, at the transmitter, the initial content of the
register of the device computing the remainder of the division is preset to
all 1s and is then modified by division by the generator polynomial (as described
above) on the address, control and information fields; the ones compliment of
the resulting remainder is transmitted as the 16-bit FCS.
At the receiver, the initial content of the register of the device computing the remainder is preset to all 1s. The final remainder, after
16
multiplication by x and then division (modulo 2) by the generator polynomial 16 12 5 of the serial incoming protected bits and the
x + x + x + 1 15 0
FCS, will be 0001110100001111 (x through x ,respectively) in the absence of transmission errors.
The 16-bit FCS is therefore generated using polynomial arithmetic as follows:
FFFF + (REM(FFFF/gen)+REM(gen/frame))
where gen = generator polynomial = 11005 hexadecimal
here is an exercise to do in the unlikely event of you having lots of time
to spare: write a program to calculate the FCS.
REM integers must contain 32 bits
CRCCONST = %H1005
DEF PROCinit
DEF bitarray(128)
checkreg = %HFFFF
pointer=1
length = 16
ENDPROC
DEF PROCexor (checkreg,crcconst)
checkreg = (checkreg AND %HFFFF) XOR crcconst
ENDPROC
DEF PROCbit
checkreg=checkreg * 2 + bitarray (pointer)
IF checkreg > %HFFFF THEN PRCexor
ENDPROC
DEF PROCdivremain
FOR pointer=1 TO length
PROCbit
NEXT
PRINT "result = ",checkreg
ENDPROC
I Information frame (SDLC and HDLC)
Coding - bit: 8 7 6 5 4 3 2 1
value: N(R) P N(S) 0
modulo 128 - bit: 8 7 6 5 4 3 2 1 8 7 6 5 4 3 2 1
value: <-- N(S) ---> 0 <--- N(R) --> P
I frames are numbered. The Ns count provides for numbering the frame being
sent and the Nr provides acknowledgement for the I frames received. When duplex
information exchange is in continual process, each station reports its current
Ns and/or Nr counts in each I or S frame exchanged.
Supervisory frames
RR - Receive Ready (SDLC and HDLC)
Coding - bit: 8 7 6 5 4 3 2 1
value: N(R) P 0 0 0 1
modulo 128 - bit: 8 7 6 5 4 3 2 1 8 7 6 5 4 3 2 1
value: 0 0 0 0 0 0 0 1 <--- N(R) --> P
Sent by either a primary or secondary station, RR confirms numbered
frames through Nr-1 and indicates that the originating station is
ready to receive.
RNR - Receive Not Ready (SDLC and HDLC)
Coding - bit: 8 7 6 5 4 3 2 1
value: N(R) P 0 1 0 1
modulo 128 - bit: 8 7 6 5 4 3 2 1 8 7 6 5 4 3 2 1
value: 0 0 0 0 0 1 0 1 <--- N(R) --> P
Sent by either a primary or secondary station, RNR indicates a
temporarily busy condition due to buffering or other internal
constraints.
REJ - Reject (SDLC and HDLC)
Coding - bit: 8 7 6 5 4 3 2 1
value: N(R) P 1 0 0 1
modulo 128 - bit: 8 7 6 5 4 3 2 1 8 7 6 5 4 3 2 1
value: 0 0 0 0 1 0 0 1 <--- N(R) --> P
This command/response may be transmitted to request transmission or
retransmission of numbered information frames. REJ confirms frames
through Nr-1 and requests the retransmission of numbered information
frames starting at the Nr contained in the REJ frame.
Unnumbered Format (SDLC only)
UI - unnumbered Information = 0 0 0 P 0 0 1 1 = X'03' or X'13'
As a command or a response, a UI frame is the vehicle for transmitting
unnumbered information.
SNRM - set normal response mode = 1 1 0 0 P 0 0 1 = X'83' or X'93'
This command places the secondary station in normal response mode
(NRM) for information transfer. UA is the expected response. The
primary and secondary station Nr and Ns counts are reset to 0. No
unsolicited transmissions are allowed from a secondary station that is
in NRM. The secondary station remains in NRM until it receives a DISC
or SIM command.
DISC - Disconnect = 0 1 0 P 0 0 1 1 = X'43' or X'53'
This command terminates other modes and places the receiving
(secondary) station in disconnected mode. The expected response is UA.
A secondary station in disconnected mode cannot receive or transmit information or supervisory frames.
RD - Request Disconnect = 0 1 0 F 0 0 1 1 = X'43' or X'53'
This request is sent by a secondary station desiring to be disconnected (by the DISC command)
UA - Unnumbered Acknowledgment = 0 1 1 F 0 0 1 1 = X'63' or X'73'
This is the affirmative response to an SNRM,DISC or SIM command
RIM - Request Initialisation Mode = 0 0 0 F 0 1 1 1 = X'07' or X'17'
A RIM frame is transmitted by a secondary station to notify the
primary station of the need for a SIM command
SIM - Set Initialisation Mode = 0 0 0 P 0 1 1 1 = X'07' or X'17'
This command initiates system-specified procedures for the purpose of
initialising link-level functions. UA is the expected response. The
primary and secondary Nr and Ns counts are reset to 0.
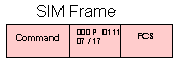
DM - Disconnected Mode = 0 0 0 F 1 1 1 1 = X'0F' or X'1F'
This response is transmitted by the secondary station to indicate that
it is in the disconnected mode.
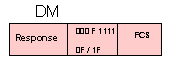
FRMR - Frame Reject = 1 0 0 F 0 1 1 1 = X'87' or X'97'
This response is transmitted by a secondary station in NRM only when
it receives an invalid frame. A received frame may be invalid for
several reasons:
* its C field is not implemented at the receiving station. This
category includes unassigned commands.
* the information field is too long to fit the receiving station
buffers
* The C field in the received frame does not allow an I field to be
received with the frame.
* The Nr that was received from the primary station is invalid.
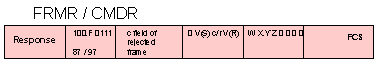
TEST - tst = 1 1 1 P 0 0 1 1 = X'E3' or X'F3'
As a command, a test frame may be sent to a secondary station in any mode
to solicit a TEST response. If an information field is included with the command
it is returned in the response.
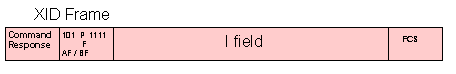
XID - Exchange station Identification = 1 0 1 P 1 1 1 1 = X'AF' or X'BF'
As a command, XID solicits the identification of the receiving (secondary) station. An information field may be included in the frame to convey identification of the transmitting (primary) station. An XID response is required from the secondary station. An information field in the response may be used for identification of the responding secondary station.
Loop Commands and responses (SDLC only)
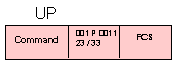
UP - Unnumbered Poll = 0 0 1 P 0 0 1 1 = X'23' or X'33'
with P bit = 0:
An optional response poll is sent out by the primary station to poll one station, a group of stations, or all the stations on the loop. A response is not necessarily required.
with P-bit = 1:
A mandatory response poll is addressed to an individual station, group of
stations, or all of the stations ona loop. It serves to perform an unnumbered
poll of the addressed secondary stations. A polled station will respond either
with frames it has waiting to transmit or retransmit, or, if no such frames
exist, with another appropriate response (RR,RNR or DM).
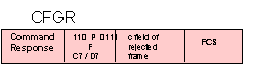
CFGR - Configure = 1 1 0 P 0 1 1 1 = X'C7' or X'D7'
Command:
The configure command contains a function descriptor (a subcommand) in a single- byte information field.
Subcommands:
00000000 Clear
0000001x Beacon test
0000010x Monitor Mode
0000100x Wrap
0000101x Self-test
0000110x Modified Link test
RESPONSE:
The configure response is transmitted by secondary stations only in response
to a configure command. The structure of the configure responses are identical
to those of the configure commands. If the low order bit in the information
field of the response is set to 1, the configure function in the information
field has been set. If the low-order bit in the information field is set to
0, the configure function in the information field has been cleared.
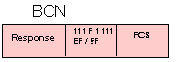
BCN - Beacon - response 1 1 1 F 1 1 1 1 = X'EF' or X'FF'
When the secondary station detects the loss of communication at its input, it begins to transmit a beacon response. This allows the primary station to locate the problem in the loop and to take appropriate action. In the beacon response, the F-bit can be either a 1 or a 0. As soon as the input resumes normal status the secondary stops transmitting the beacon response.
SDLC - procedures
Like other IBM protocols such as bi-sync, SDLC works in a polling environment
this allows a point-to-point link or a multiple station loop configuration consisting
of a primary station and a number of secondary stations.
Any commands sent by the host with the P bit set are polls and must be responded
to by the terminal with the address specified. An I frame can be sent without
the P bit, this indicates that there is more I-frame(s) to come and therefore
the other end should not respond.
The P/F bit can therefore be thought of as indicating that the direction of transmission can be turned round. SDLC can therefore theorectically work
half-duplex.
SDLC - activating link
Bringing a link up (SDLC)
Primary Secondary
------- 01 SNRM P (command) ------>
primary ------- 02 SNRM P (command) ------> secondary
station stations
(host end) ------- 01 SNRM P (command) ------> (terminal
ends)
<------ 01 UA F (response) --------
------- 01 RR P (command) ------>
------- 02 SNRM P (command) ------>
This example shows the primary station polling devices 01 and 02 with
SNRM's with the P-BIT set to 1, secondary station then becomes ready it
responds with a UA with the P-BIT set to 1. station 01 will then be polled
with RRs and station 02 will continue to be polled with SNRMs.
Taking Line Down
Initiated by primary station -
Primary Secondary
------- ---------
------ DISC P (command) ------->
<----- UA F (response) --------
Initiated by secondary station -
------ RR P (command) --------->
<----- RD F (response) -------- | Request disconnect
------ DISC P (command) ------->
<----- UA F (response) --------
13 - SDLC Information Transfer
primary to secondary -
------- I P (command) --------->
<------ RR F (response) -------
Primary can send an I frame at any time the link is up, the secondary can
acknowledge this with either of RR,RNR,REJ or I frames.
secondary to primary -
------- RR P (command) --------> | Poll
|
<------ RR F (response) -------- | Nothing to
| send
------- RR P (command) --------> | Poll
|
<------ I (response) -------- | 1 to 7 I frames
| depending on
<------ I (response) -------- | window size can
| be seniin response
<------ I F (response) -------- | to poll
| final I frame has F
| bit to indicate
| turn round of line
Although X.25 frame types are similar to SDLC, commands and responses and
the P-bit are used completely differently from SDLC.
The protocol is more either end can initiate transmission
\ 4 0 0 0 0 1 1 1 1
\ 3 0 0 1 1 0 0 1 1
\ 2 0 1 0 1 0 1 0 1
876 -------------------------------------------------------------
000 RR *UI RNR *RIM/SIM REJ *SRJ SARM
001 RR *UP RNR REJ *SRJ SABM
010 RR DISC RNR REJ *SRJ
011 RR UA RNR REJ *SRJ
100 RR *SNRM RNR FRMR REJ *SRJ *RSET
101 RR RNR REJ *SRJ
110 RR RNR *CGR REJ *SRJ
111 RR *TEST RNR REJ *SRJ *BCN


